Cybersecurity Services
With our extensive experience and proven track record, we’re here to ensure your cybersecurity needs are not just met but exceeded.

Always Evolving to Meet Cybersecurity Threats
When it comes to cybersecurity, you need a partner who continuously learns and evolves to address the latest threats. Managing cybersecurity in-house can be challenging, as the scope of threats is constantly changing, making it difficult for an internal team to stay current.
Trust Your Cybersecurity to Experts
With WingSwept, your cybersecurity is in capable hands. Our team has extensive experience in various industries, allowing us to tailor solutions to your specific needs. Focus on driving your business forward, knowing that your cybersecurity is managed by experts.
Proactive Cybersecurity Protection
Ensuring your business is protected against common cybersecurity threats requires a proactive approach. Partnering with us means going beyond the basics to implement tailored security standards that safeguard your business.
Customized Solutions for Your Industry
Our extensive cybersecurity experience allows us to tailor security standards to your specific industry and business needs. We assess your current security posture, identify areas for improvement, and implement measures that align with industry best practices, ensuring your cybersecurity is always up to date.
Expert Cybersecurity Monitoring
At WingSwept, we understand the critical importance of maintaining robust cybersecurity in an era where digital threats are constant. Our comprehensive security monitoring services are meticulously designed to offer you unparalleled protection, ensuring that your data and operations remain as secure as possible.
While internal cybersecurity teams have the advantage of intimate knowledge of their specific environment, they often lack the breadth of experience that third-party providers can offer. WingSwept brings a diverse perspective and extensive experience across various industries, enabling us to detect and neutralize threats that might elude an internal team. Our external viewpoint allows us to stay ahead of emerging threats and provide a more comprehensive security solution.
With an average tenure of over 11 years, our cybersecurity engineers reflect dedication and expertise in the field. This extensive experience enables our team to provide exceptional security monitoring services, informed by a deep understanding of both common and sophisticated threats. Our engineers’ long-term commitment to WingSwept ensures continuity and reliability in the protection of your business.
Adhering to the highest cybersecurity standards ensures your business is protected by the most stringent protocols. Our commitment to excellence is demonstrated through our use of advanced threat detection tools, regular security audits, and tailored best practices designed to meet your specific needs.
We believe in empowering our clients with the knowledge they need to make informed decisions about their cybersecurity. Our approach includes educating companies about their specific security risks, helping them understand the threats they face and the measures needed to mitigate them. By providing tailored insights, we guide businesses to invest appropriately in their security measures, avoiding both underinvestment and unnecessary expenses.
Cybersecurity Incident Response
Despite all preventative measures, complete security is impossible because the weakest link is often the human factor. When cyber incidents occur, WingSwept’s Incident Response services are your best chance to mitigate the negative impacts. Our expert team swiftly addresses breaches to minimize damage and restore normal operations, helping your business stay resilient against evolving threats.
Executive-Level Guidance
Our consultative approach includes executive-level guidance to help you navigate the complexities of cybersecurity. Our senior experts are available to provide personalized advice and strategic insights tailored to your business needs. Whether you need to discuss specific concerns or develop a long-term security strategy, our team is here to support you.
Proactive Measures
Our commitment to proactive cybersecurity measures sets us apart. We have a defined compromised response process that allows us to quickly identify and address vulnerabilities in your system. By continuously monitoring your IT environment and implementing the latest security protocols, we can prevent many incidents before they occur. Our proactive measures are designed to keep your business secure and resilient against emerging threats.
Preparedness through Practice
At WingSwept, we believe that preparation is key to effective incident response. Our team conducts regular tabletop exercises to simulate various cyberattack scenarios. These exercises prepare our team to act decisively and effectively when real incidents occur. This proactive approach allows us to refine our response strategies continuously, ensuring we are always ready to protect your business.
Comprehensive Managed Security
Incident response is not just an add-on service for us; it's an integral part of our comprehensive managed security offerings. We provide end-to-end security solutions that cover every aspect of your IT infrastructure. From regular security assessments to continuous monitoring and incident response, we aim to keep your business protected at all times.
Swift and Strategic Response
When a cyber incident occurs, time is of the essence. Our incident response team is trained to act quickly, containing and mitigating threats before they can cause significant damage. We analyze breach examples and use our extensive experience to apply the most effective response tactics. Our strategic approach ensures that we minimize downtime and reduce the impact on your business operations.

Advanced Security Tools
Read More >
Advanced Security Tools
These tools form a comprehensive defense strategy, enabling us to detect, analyze, and respond to threats effectively. By leveraging cutting-edge technology, we fortify your digital defenses to keep your business secure in an ever-changing threat landscape.
Ongoing approach
Cybersecurity is an ongoing process, not a one-time task. Our approach involves layering multiple levels of protection to safeguard your business comprehensively. We prioritize continuous monitoring, regular updates, and proactive communication to maintain your systems’ security and keep you informed.
Don't Take Our Word For It
“My company has been with WingSwept several years now and during that time they have always been johnny on the spot” when responding to our needs whether simple or urgent. During this time I have never witnessed any of them loose their patients when working with our employees and yet at times you feel certain they will (and have a right to!) The integrity I have witnessed in WingSwept stands far and above any other IT company we have done business with.”
Explore Tailored
Cybersecurity Solutions
What happens Next?
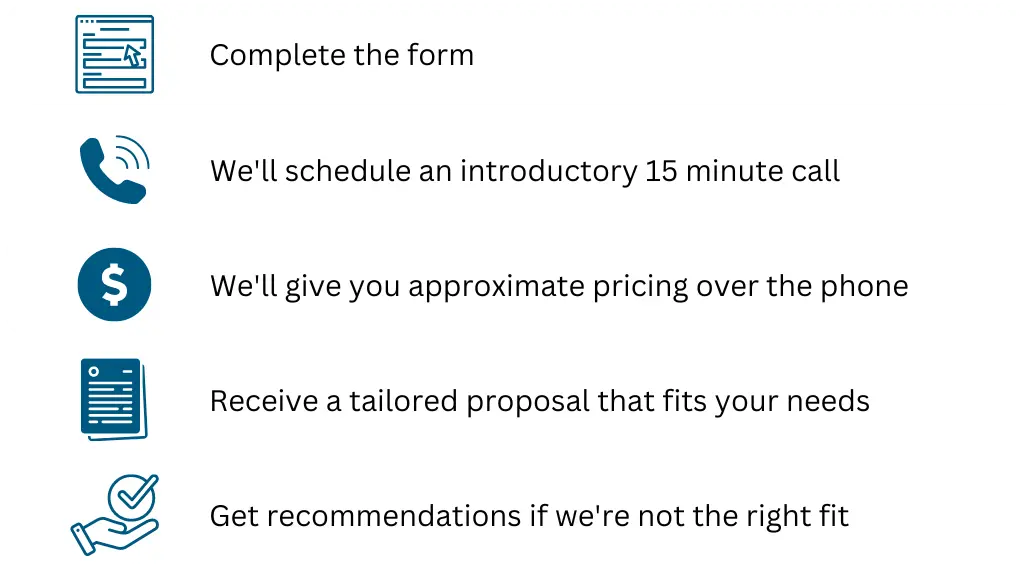
Embark on the path to fortify your cybersecurity defenses today. Fill out the form below to start a no-pressure, informative discussion. Our team is prepared to provide insights and expertise tailored to your needs. If our services aren’t the right fit, we’ll gladly recommend alternative solutions.





